Which Of The Following Attack Compromises Availability
Which Of The Following Attack Compromises Availability - There are different types of network attacks aimed at three pillars of network security; Q5.which of the following attack compromises confidentiality? (choose two options) a.denial of service attack b.keylogger. Denial of service and ransomware attacks compromise system availability, while disclosing passwords primarily affects.
Q5.which of the following attack compromises confidentiality? (choose two options) a.denial of service attack b.keylogger. There are different types of network attacks aimed at three pillars of network security; Denial of service and ransomware attacks compromise system availability, while disclosing passwords primarily affects.
Q5.which of the following attack compromises confidentiality? Denial of service and ransomware attacks compromise system availability, while disclosing passwords primarily affects. There are different types of network attacks aimed at three pillars of network security; (choose two options) a.denial of service attack b.keylogger.
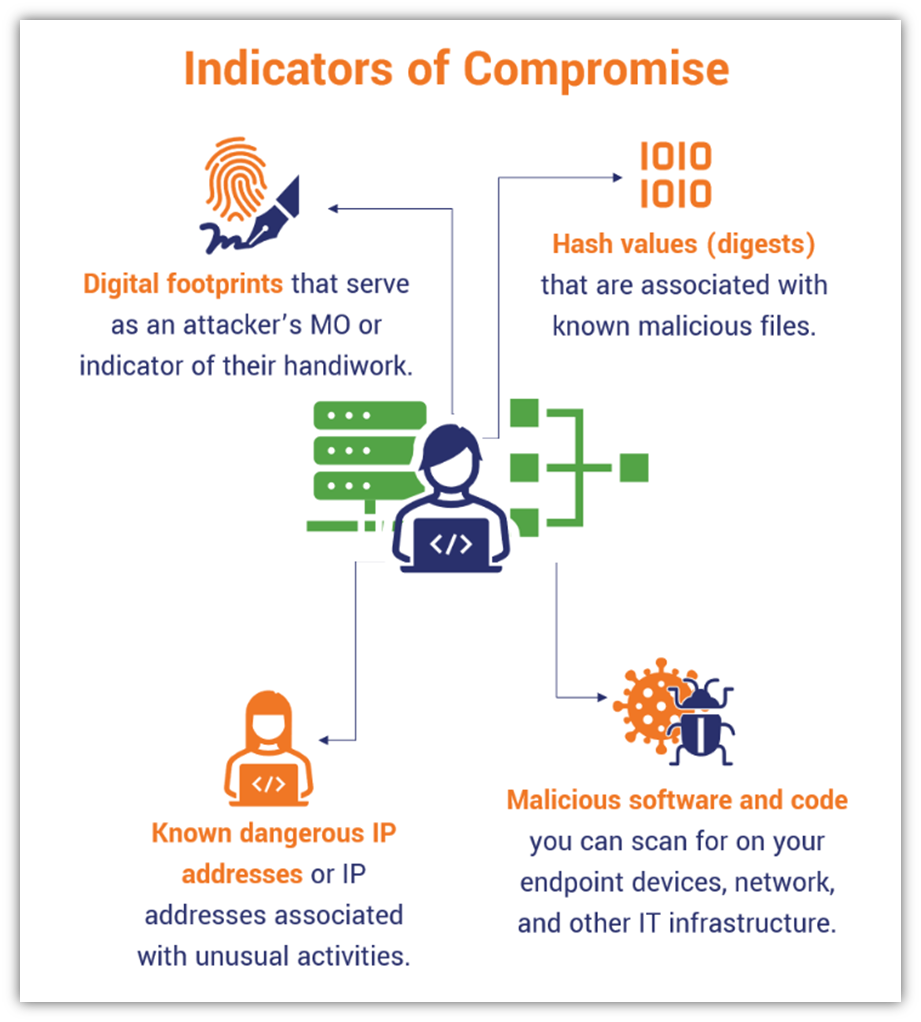
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed
Q5.which of the following attack compromises confidentiality? There are different types of network attacks aimed at three pillars of network security; (choose two options) a.denial of service attack b.keylogger. Denial of service and ransomware attacks compromise system availability, while disclosing passwords primarily affects.
CS 591 Introduction to Computer Security ppt download
There are different types of network attacks aimed at three pillars of network security; Denial of service and ransomware attacks compromise system availability, while disclosing passwords primarily affects. Q5.which of the following attack compromises confidentiality? (choose two options) a.denial of service attack b.keylogger.
Solved Which of the following attack compromises
There are different types of network attacks aimed at three pillars of network security; (choose two options) a.denial of service attack b.keylogger. Denial of service and ransomware attacks compromise system availability, while disclosing passwords primarily affects. Q5.which of the following attack compromises confidentiality?
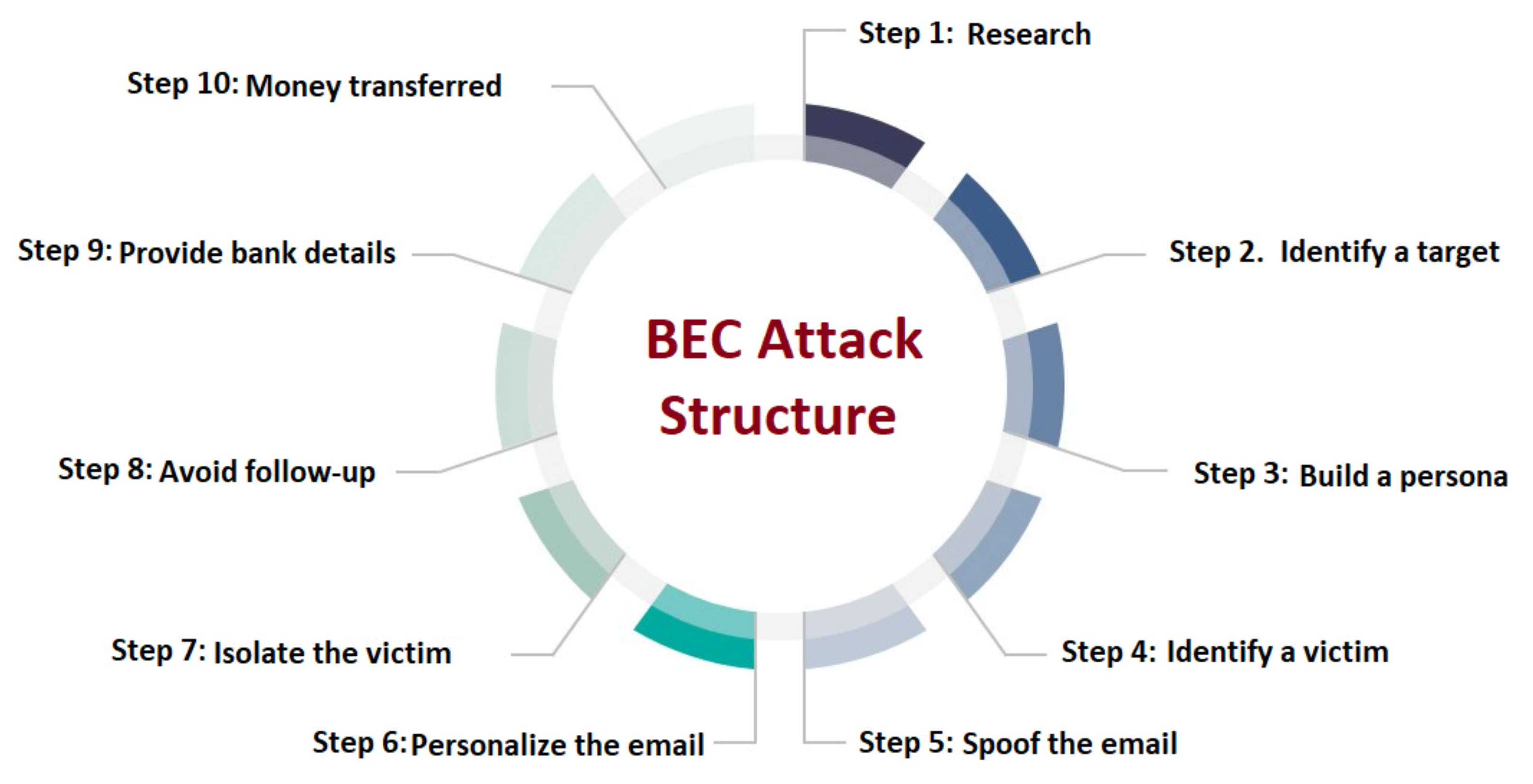
INFOGRAPHIC Recognizing and Avoiding Business Email Compromise Attacks
(choose two options) a.denial of service attack b.keylogger. Denial of service and ransomware attacks compromise system availability, while disclosing passwords primarily affects. There are different types of network attacks aimed at three pillars of network security; Q5.which of the following attack compromises confidentiality?
Solved Which of the following attack compromises availability? a
Q5.which of the following attack compromises confidentiality? Denial of service and ransomware attacks compromise system availability, while disclosing passwords primarily affects. (choose two options) a.denial of service attack b.keylogger. There are different types of network attacks aimed at three pillars of network security;
Today’s topics Demo from RSA Security ( ppt download
Q5.which of the following attack compromises confidentiality? There are different types of network attacks aimed at three pillars of network security; Denial of service and ransomware attacks compromise system availability, while disclosing passwords primarily affects. (choose two options) a.denial of service attack b.keylogger.
Cyber Threats Part 1 Understanding the Cyber Attack Cycle TSG
Denial of service and ransomware attacks compromise system availability, while disclosing passwords primarily affects. (choose two options) a.denial of service attack b.keylogger. There are different types of network attacks aimed at three pillars of network security; Q5.which of the following attack compromises confidentiality?
Indicators of Compromise Cybersecurity’s Digital Breadcrumbs Hashed
(choose two options) a.denial of service attack b.keylogger. There are different types of network attacks aimed at three pillars of network security; Denial of service and ransomware attacks compromise system availability, while disclosing passwords primarily affects. Q5.which of the following attack compromises confidentiality?
Business Email Compromise Phishing Detection Based on Machine Learning
There are different types of network attacks aimed at three pillars of network security; (choose two options) a.denial of service attack b.keylogger. Denial of service and ransomware attacks compromise system availability, while disclosing passwords primarily affects. Q5.which of the following attack compromises confidentiality?
Common Security Attacks in the OSI Layer Model
There are different types of network attacks aimed at three pillars of network security; Q5.which of the following attack compromises confidentiality? Denial of service and ransomware attacks compromise system availability, while disclosing passwords primarily affects. (choose two options) a.denial of service attack b.keylogger.
There Are Different Types Of Network Attacks Aimed At Three Pillars Of Network Security;
Denial of service and ransomware attacks compromise system availability, while disclosing passwords primarily affects. (choose two options) a.denial of service attack b.keylogger. Q5.which of the following attack compromises confidentiality?